Microsoft Defender Deployment and Management
Contact UsWhat We Do
- Our Microsoft security services start with understanding your business needs, risk, license levels, existing toolset, and budget to maximize your investment in Microsoft security products (“Microsoft Security” encompassing Microsoft XDR, Microsoft Defender for business, and Azure Active Directory)
- Evaluate the functionality and cost of Microsoft Security with your current security and IAM stack to improve security effectiveness and efficiency, and drive progress towards operating and compliance frameworks, for example the Zero Trust security model
- Design security deployments of Microsoft Security with controlled testing groups and phased rollout plans to reduce organizational and user risk
- Assess and configure Microsoft 365 security and Microsoft cloud security tools based on leading benchmarks and compliance standards
- Continuously validate that secure configurations are maintained using SecureSky’s security posture management platform (Microsoft CSPM and Microsoft SSPM)
- Collect and correlate Microsoft Security threat detection signals into the Microsoft SIEM, Microsoft Sentinel, to amplify visibility and correlation across the organization and streamline threat response
- Provide ongoing Managed XDR/Defender services (MXDR), integrated with our Managed Detection and Response (MDR) practice area
- Intune Mobile Device/Endpoint and Mobile Application Management
- OMS/AMA Agent
- Defender for Identity (Active Directory)
- Third-Party Security Products
- Logic Apps/Workflow Automation
- Information Protection
- Defender for Cloud Apps (CASB)
- Conditional Access Policies
- Defender for O365
- O365 Security and Compliance
- Application Connections and Consents
- Privileged Identity Management
- Active Directory Services
- Conditional Access Policies
- Security & Compliance Score
- Azure Policies Information Protection
- Cost Management
- Front Door
- Defender for IoT / Servers / Storage / Identity / Cosmos DB / Kubernetes / MS SQL / Containers
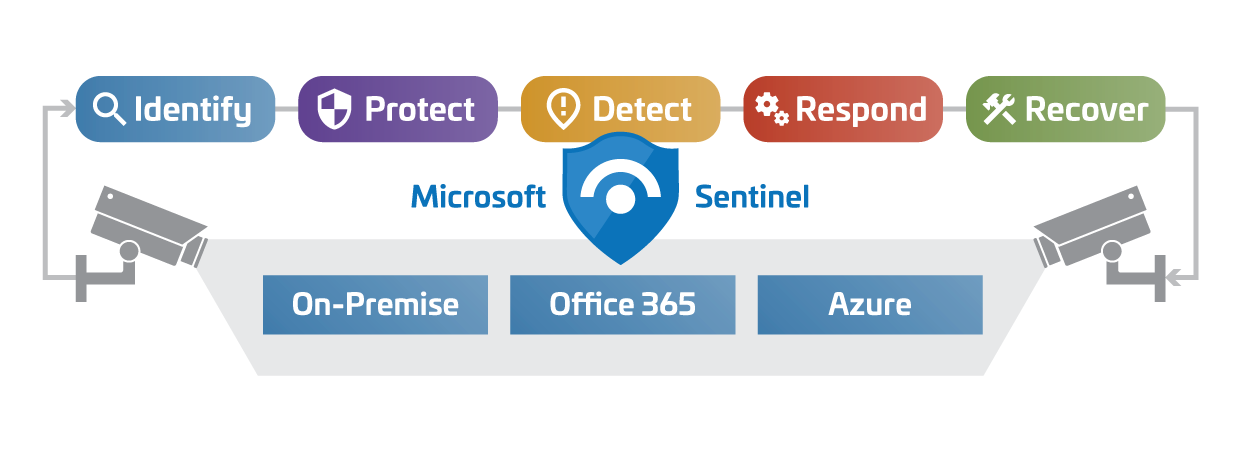
Microsoft Defender, Azure AD, and Microsoft Sentinel
High Level of Microsoft's Current Organization of XDR/Defender Security Services
Microsoft 365 Defender
In the past several years, Microsoft has developed into a major security player, with the substantial magnitude of their email, productivity tools, and Windows operating system (and related security functionality) collecting and analyzing trillions of security signals and protecting billions of systems daily. In a similar timeframe, Microsoft, like most software providers, has also migrated from selling boxed software to a SaaS subscription model.
As Microsoft and Microsoft Security have evolved, they have made numerous revisions to branding, product categories, product names and licensing options (see FAQs below for more information).
While these multiple gyrations to naming conventions might be confusing, nothing should deter buyers from recognizing the powerful capabilities of Microsoft Security, and the advantages gained from closely integrating identity, device, and cloud (IaaS and SaaS) security controls and threat detection.
Microsoft’s current organization of XDR/Defender services is including Microsoft XDR, Azure AD, and Microsoft Sentinel is shown to the left.
Check out the SecureSky blog for more articles and resources on the various Defender technologies.
Azure Active Directory (Azure AD) and Conditional Access Policies
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management (IAM) service. Azure AD can be enabled to control IAM for external (such as integrated SaaS applications) and internal resources (such as proprietary applications or services).
While IAM is a cornerstone of any security program, Azure AD is not included in the XDR (Extended Detection and Response) category, which, by its definition, is focused on threat data detection, collection, correlation, analysis, and response across an enterprise’s information assets.
Microsoft XDR and Azure AD belong in the same conversation however, because every Microsoft 365 and Azure tenant (the underlying services of Microsoft XDR) is automatically an Azure AD tenant, and Azure AD can use risk from Defender technologies (most often Defender for Identity and Defender for Cloud Apps) as a condition of access.
These conditions of access are called Conditional Access Policies, which can keep users and data safe, even if their credentials have been compromised, by determining, based on type of user, user location, the type and state of the user device, the application attempting to be accessed, and the above-mentioned risk detection, whether to grant access, block access, or require additional steps, such as MFA.
Microsoft Sentinel SIEM
An added benefit of utilizing the Microsoft Security suite is its integration with the Microsoft Sentinel SIEM, allowing users to stream security incidents into a common aggregator, with enough alert, entity, and enrichment context to perform triage and streamline response. Once in Sentinel, incidents synchronize bi-directionally between portals.
Many organizations use Microsoft Sentinel as a primary incident queue, providing visibility and correlation with incidents across other across their entire organization, while taking advantage of Defender portals for additional enrichment data, in-depth investigations, or forensic data collection.
For more information about Microsoft Sentinel, please see link.
Making It Work
To take advantage of the security features and integrated functionality of the rapidly changing Microsoft Security suite, these capabilities must be properly designed, configured, and deployed, considering the business needs, risk and existing technology stack of the organization.
01
SecureSky has a practical understanding of the the Microsoft Security suite and competitive technologies and assists organizations with well-defined and implementations of their licensed toolset. This includes evaluation of the current environment and tools, including strengths and gaps in coverage, security controls, and threat detection policies.
Initial planning will be coordinated with the Microsoft Sentinel roadmap, to ensure visibility and protections extend across the XDR control plane.
02
SecureSky’s Microsoft experts often begin with strengthening protections in device, SaaS access, and IAM controls by enabling baselines for Defender for Endpoint, Defender for Cloud Apps. Defender for Identity, and Azure AD Conditional Access Policies.
Once these baseline policies have been deployed and tuned, SecureSky assists with customizing Defender policies and configurations, and enabling additional Microsoft Security functionality based on specific client environments, use cases, or risk factors.
03
Because of the complexities involved in properly deploying these tools, including possible conflicts or needed exclusions between technologies or policies, it is critical that a thorough process be followed, which includes definition of objectives, detailed planning, test group segmentation and monitoring, iterative tuning, and controlled rollout.
SecureSky’s methodology and experience supports these important phases, greatly reducing project risk and helping to ensure success.
We Hunt Differently.
We Reduce Threats.
Bringing It All Together
As described earlier, many organizations, including SecureSky, utilize Microsoft Sentinel to bring together Microsoft Security incidents and related threat and risk data, to manage a common event queue, increase SecOps efficiencies by employing common infrastructure and automations, and increase security effectiveness gained from inter-connected threat signals, policies and alerting.
SecureSky’s Proactive Managed Security Services use the integrated Microsoft platform in providing Managed Detection and Response (MDR) together with Microsoft Security deployment, enablement, and management (Managed XDR or MXDR) services.
Frequently Asked Questions
What is cloud security?
Cloud security is inclusion of cloud environments (IaaS, PaaS, and SaaS) into an organization’s Enterprise Security Program, including continuous risk management, the application and adaption of protective controls to ensure confidentiality, integrity and availability of resources, and threat detection and response performed in a resilient manner, to rapidly withstand and recover from malicious attacks. Dependent on the organization’s usage of cloud resources, the responsibility for risk management, protective controls, and threat response is shared between the cloud provider and customer.
Who needs cloud security?
As published by every major cloud provider, the “shared responsibility” model communicates to all customers of cloud services their accountability for multiple elements of cloud security. Based on their usage of cloud infrastructure, platform, or software services, customers are liable for appropriately configuring security controls and threat detection policies for their applications, data, and user identities and access.
What are the benefits of cloud security?
As with all cybersecurity measures, whether to protect cloud or on-premises environments, the benefits of cloud security are maintaining the confidentiality and integrity of input and derived data, the efficacy of processes, and the availability of resources. Properly securing a company’s digital assets provides efficiency (with related cost savings) for an organization’s internal users, and, if applicable, reliability (with related competitive advantages) for external users.
What are the challenges in cloud security?
There are numerous challenges in cloud security, beginning with awareness of an organization’s presence in the cloud. Often coined “shadow IT”, it is very simple for users to spin up cloud or SaaS instances in a matter of minutes, without a thorough understanding of security protocols. The nature of cloud computing also dissolves traditional network boundaries, leading to user identification, access and entitlement management becoming the focal point of controls, as well as user behaviors often being a primary indicator of risk. Another challenge is the sheer volume of cloud usage. The recent COVID-19 pandemic accelerated the already rapidly growing adoption of cloud computing. Only counting SaaS applications, estimates range from an average company using between 80 to 140 different applications. This “SaaS sprawl” and related explosion of all cloud services makes multi-cloud monitoring and management almost impossible. Finally, as in all cybersecurity fields, the shortage of human resources with cloud security expertise, especially as attack volumes grow daily, is a major concern.
What are the types of cloud security?
There are many categories of products and services that can be used to secure cloud environments, many of which are cloud-based services themselves. These include tools for user identification, controlled access, entitlement management, email phishing or malware deterrence, data loss prevention, limiting access to risky applications, and IaaS and SaaS secure configuration management (cloud security posture management).
What is a cloud security model?
An effective cloud security model incorporates several integrated technologies and intelligence sources, with automation and adaptive response capabilities. At the core of this model is the “Zero Trust” principle. Traditional network-based Zero Trust says that users, systems or services operating inside the network must be identified and authenticated with each system or service they are attempting to access. In today’s cloud computing world, where there are more users, systems or services outside an enterprise than inside it, attempting to access the cloud with more unmanaged than managed devices, this principle is modified to say that access to cloud features and data must be consistently verified before being trusted.
Why is SaaS security important?
A startling statistic for every CIO and CISO – estimates of the number of SaaS applications used by an average organization today range between 80 to 140 different applications. In addition to sheer volume, very often these applications, in categories such as ERP, HR, CRM, and R&D, contain an organization’s most confidential data. While the confidentiality, integrity, and availability of SaaS applications is critical to most businesses, this “SaaS sprawl” makes securing SaaS very challenging, especially given today’s shortage of cybersecurity resources. Securing SaaS applications should often be a primary goal of a proactive Enterprise Security Program, and yet we find there continues to be major gaps in understanding of user’s responsibilities and proper attention paid to setting and continuously validating SaaS security configurations.
How do you manage security in the cloud?
In cybersecurity overall, the no-win approach of constantly reacting to threats is no longer practical, especially in these days of scarce security resources. In addition to best practices, cloud security management includes integration, automation, and adaption, focusing efforts and spending on attack surface reduction, or preventing attacks by hardening security controls, lowering risk, threat volumes, and overall costs.
How does Microsoft brand their security suite?
In the past several years, Microsoft has developed into a major security player, with the substantial magnitude of their email, productivity tools, and Windows operating system (and related security functionality) collecting and analyzing trillions of security signals and protecting billions of systems daily. In a similar timeframe, Microsoft, like most software providers, has also migrated from selling boxed software to a SaaS subscription model.
As Microsoft and Microsoft Security have evolved, they have made numerous revisions to branding, product categories, product names and licensing options. A few gyrations include replacing Azure with Microsoft in several product categories, the evolution of Microsoft Office to Office 365 to Microsoft 365, using license levels such as “E5” and “P2” to describe technology capabilities, employing “XDR” as a solution set and later as an umbrella for the Defender series, the ultimate unifying of XDR technologies under the “Defender” brand, and the introduction of additional functional collections such as Microsoft Entra and Microsoft Purview.
While these changing naming conventions might be confusing, they should not deter buyers from recognizing the powerful capabilities of Microsoft Security, and the advantages gained from closely integrating identity, device, and cloud (IaaS and SaaS) security controls and threat detection.
Do I need a specific Microsoft 365 license to use Sentinel?
Microsoft Sentinel will work with any M365 license. The standard M365 workloads (Exchange, SharePoint, and Teams) activity will integrate with Microsoft Sentinel regardless of license. As you “move up” the license structure of M365, additional security logging and integration will be available (for example, evidence collected from the Defender suite).
Azure Active Directory integration into Microsoft Sentinel requires at least AAD Premium P1 licensing, which is bundled into several M365 license plans or can be acquired individually.
I utilize other security products outside of the Microsoft Security suite. Can I still utilize Microsoft Sentinel?
Absolutely! Microsoft Sentinel integrates with most major security vendors.
Have More Questions?
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.
