Full Lifecycle Cloud Security
Contact Us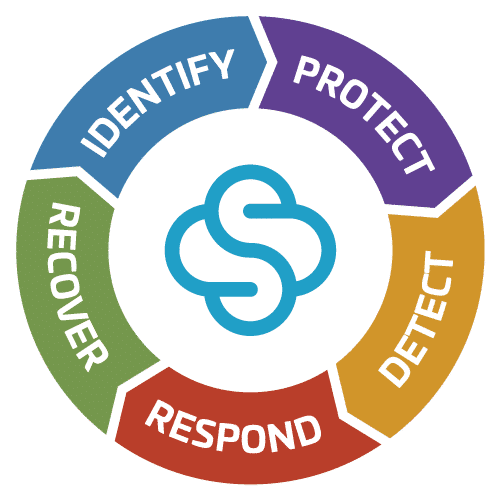
SecureSky cloud-based security solutions align with today’s most commonly accepted frameworks and methodologies. SecureSky offers services in all areas of the security lifecycle, partners with your organization to understand your requirements, and provides managed detection and response services.
Whether your security goal is identifying and managing risk, detecting and responding to threats, or advanced measures to test and optimize the controls you have in place, SecureSky can help.
We understand that our clients have businesses to run, with objectives and timelines. When we say that we will deliver by a certain date, we will do everything in our power to do so, and keep you fully apprised along the way.
Our practical approach will also align with your budget. Our solutions are delivered and invoiced in a cost effective, transparent manner, with no surprises or unexpected charges.
IDENTIFY
Discovery and assessment of risk across an organization’s cloud stack. Utilizing best practices and cloud native controls with recommendations that allow for practical remediation and governance.
PROTECT
Definition, design and hands-on implementation of security hardening standards, protection technologies and in-depth training of client personnel.
DETECT
Monitoring, managed detection, and response services with ongoing policy testing and validation to ensure compliance with security best practices.
RESPOND
Continuous event investigation and incident response, takedown, forensic support services and interface with law enforcement.
RECOVER
Retrospective review for tuning and risk protection optimization, to ensure continuous security improvement.
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.
