BEC / ATO Incident Response
Comprehensive Cyber Security Consulting for BEC Response and Cloud Incident Management Contact UsWhat We Do
- Assess protective controls and detection policies versus security benchmarks, best practices and compliance standards
- Validate compensating controls and actual risk through cyber security consulting
- Actionable recommendations to strengthen the environment
- Assist with remediation design, deployment and testing
Specialized Cloud Incident Response
Each SecureSky cloud incident response engagement includes:
- Incident containment and management
- Forensic data capture
- Communication processes built on years of incident response experience
- Recommendations for remediation to reduce future incidents and to improve detection and response capabilities
Incident Response for Business Email Compromise (BEC) or Account Takeover (ATO)
Increased usage of cloud infrastructure necessitates understanding new attack techniques and formulating incident response processes that differ from traditional incident response methods. Additionally, growth in multi-tenant SaaS or subscription models has allowed the malicious use of compromised environments to potentially expand to multiple organizations, making incident containment much more challenging.
SecureSky specializes in cloud incident response and forensic investigation, using proprietary cloud-native tools and techniques, which enable our clients to triage an attack more quickly and reduce the impact. SecureSky also assists our clients in communication with internal teams, vendors, customers and law enforcement during and subsequent to an incident. Finally, SecureSky’s expertise in cloud protective controls also assists our clients in the recovery phase, implementing root cause changes to prevent a recurrence.
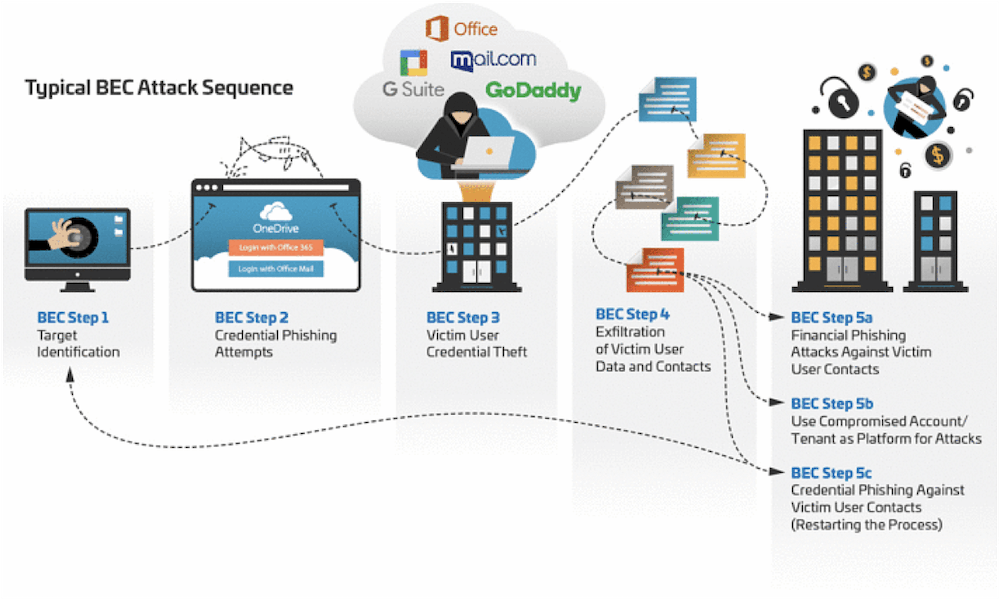
When a breach occurs, time is of the essence. Organizations cannot afford to spend time learning cloud mitigation techniques or new cloud-native tools during their response.
SecureSky provides cloud-based incident response services, which differ from traditional endpoint-based response techniques. We have the specific expertise and methodologies which let us “follow the trail” in order to contain and mitigate such attacks.
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.
