A CSPM Platform Built for Multi-Cloud
SecureSky’s Active Protection Platform goes beyond commonplace Cloud Security Posture Management (CSPM) offerings. With continuous configuration validation, available enforcement functionality, capture of threat data, and automated threat response capabilities, the unified platform provides advanced capabilities to secure your cloud presence.
Patented technology protects across multiple SaaS, PaaS and IaaS environments, providing centralized security and compliance management, to greatly simplify cloud management for security teams. Configuration and detection policy assessment, based on Center for Internet Security (CIS) Benchmarks and best practices, prioritizes risk mitigation across all cloud accounts.
Through 2023, at least 99% of cloud security failures will be the customer’s fault … organizations implementing CSPM, and extending this into development, will reduce cloud-related security incidents due to misconfiguration by 80%.

Continuous Risk and Threat Visibility, Control and Automated Protection
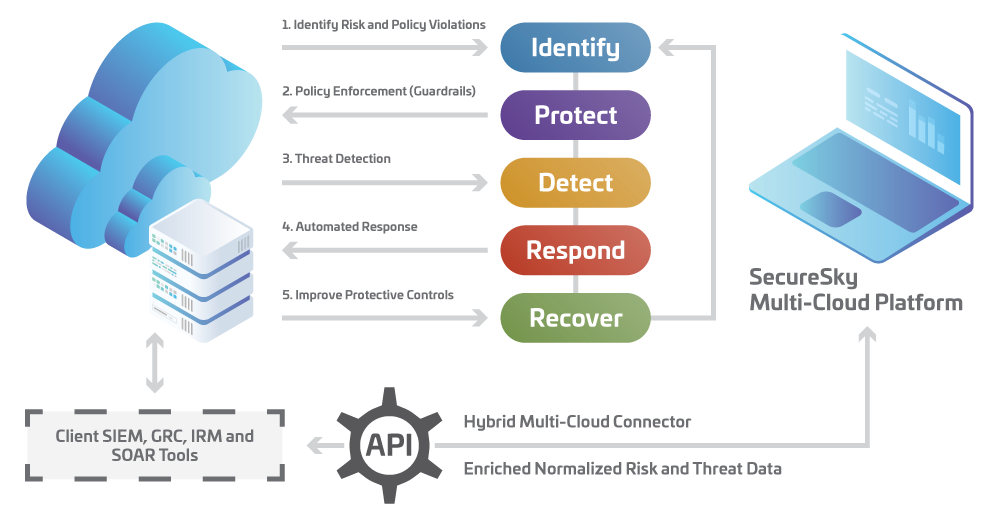
Active Protection Platform Key Features
- Real-time visibility of multi-cloud environments
- Continuous security and compliance configuration and detection policy assessment, based on industry-leading benchmarks
- Available one-click or automated enforcement of security hardened standards
- Collection of threat data
- Streamlined and automated threat response actions
- Query capabilities of configuration data to support Operations, Compliance, Incident Response, and Security Teams
For a deeper dive into the Active Protection Platform, see Active Protection Platform Technology.
Schedule a Demo
For a no-cost, no-hassle demonstration of our platform, please fill out the form below.
Frequently Asked Questions
What is SaaS security posture management?
SaaS security posture management (SSPM) is an important element of an organization’s management of their cloud-based application utilization. SSPM is an automated tool used to assess and identify risk by evaluating security configurations and detection policies, typically against a proven hardened benchmark, as well as user account permissions and activities, application connections, and plug-ins.
Advanced SSPM platforms such as SecureSky’s patented Active Protection Platform, offer continuous or runtime assessment, incorporation of threat data into risk or exposure evaluation, and response functionality including enforcement or modification of security controls and trust-based interaction with users.
What is cloud security posture management?
Cloud security posture management (CSPM) is an automated tool used to assess and identify risk by evaluating security configurations and detection policies across cloud services, including Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS). The CSPM category of security tools can also include analysis of Software-as-a-Service (SaaS), if not denoted as SSPM (described above).
Settings are analyzed against an accepted benchmark or set of best practices and can often include multi-cloud assessment and risk prioritization. Beyond this basic functionality (which Gartner coins, “scan-based” CSPM tools), advanced CSPM platforms such as SecureSky’s patented Active Protection Platform, offer continuous or runtime assessment, the correlation of threat data into risk or exposure evaluation, and response or remediation functionality, including enforcement or modification of security controls and interactive users actions.
What’s the difference between Azure Secure Score and Microsoft Secure Score?
Secure Score functionality helps companies understand their current security posture and provides a list of recommendations to proactively improve it. Both Microsoft Secure Score and Azure Secure Score play a role in enabling a holistic security posture for an organization.
Microsoft Secure Score is available in the Microsoft 365 Security Center and helps improve a security posture with regards to Microsoft 365 services. Findings are organized into groups which include Identity (Azure Active Directory accounts and roles), Devices (covered by Microsoft Defender for Endpoint), and Apps (email and cloud apps, including Office 365 and Microsoft Defender for Cloud Apps).
Azure Secure Score is available in the Microsoft Defender for Cloud dashboard and helps improve a security posture with regards to Azure resources (IaaS and PaaS) and even hybrid and multi-cloud workloads (for example, AWS and GCP resources).
If you would like to know more about how these scores are derived, visit: https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/azure-secure-score-vs-microsoft-secure-score/ba-p/2459684#
What is cloud security?
Cloud security is inclusion of cloud environments (IaaS, PaaS, and SaaS) into an organization’s Enterprise Security Program, including continuous risk management, the application and adaption of protective controls to ensure confidentiality, integrity and availability of resources, and threat detection and response performed in a resilient manner, to rapidly withstand and recover from malicious attacks. Dependent on the organization’s usage of cloud resources, the responsibility for risk management, protective controls, and threat response is shared between the cloud provider and customer.
Who needs cloud security?
As published by every major cloud provider, the “shared responsibility” model communicates to all customers of cloud services their accountability for multiple elements of cloud security. Based on their usage of cloud infrastructure, platform, or software services, customers are liable for appropriately configuring security controls and threat detection policies for their applications, data, and user identities and access.
What are the benefits of cloud security?
As with all cybersecurity measures, whether to protect cloud or on-premises environments, the benefits of cloud security are maintaining the confidentiality and integrity of input and derived data, the efficacy of processes, and the availability of resources. Properly securing a company’s sensitive data and other digital assets provides efficiency (with related cost savings) for an organization’s internal users, and, if applicable, reliability (with related competitive advantages) for external users.
What are the challenges in cloud security?
There are numerous challenges in cloud security, beginning with awareness of an organization’s presence in the cloud. Often coined “shadow IT”, it is very simple for users to spin up cloud or SaaS instances in a matter of minutes, without a thorough understanding of security protocols. The nature of cloud computing also dissolves traditional network boundaries, leading to user identification, access and entitlement management becoming the focal point of controls, as well as user behaviors often being a primary indicator of risk. Another challenge is the sheer volume of cloud usage. The recent COVID-19 pandemic accelerated the already rapidly growing adoption of cloud computing. Only counting SaaS applications, estimates range from an average company using between 80 to 140 different applications. This “SaaS sprawl” and related explosion of all cloud services makes monitoring and management of multiple cloud environments almost impossible. Finally, as in all cybersecurity fields, the shortage of human resources with cloud security expertise, especially as attack volumes grow daily, is a major concern.
What are the types of cloud security?
There are many categories of products and services that can be used to secure cloud environments, many of which are cloud-based services themselves. These include tools for user identification, controlled access, entitlement management, email phishing or malware deterrence, data loss prevention, limiting access to risky applications, and IaaS and SaaS secure configuration management (CSPM).
What is a cloud security model?
An effective cloud security model incorporates several integrated technologies and intelligence sources, with automation and adaptive response capabilities. At the core of this model is the “Zero Trust” principle. Traditional network-based Zero Trust says that users, systems or services operating inside the network must be identified and authenticated with each system or service they are attempting to access. In today’s cloud computing world, where there are more users, systems or services outside an enterprise than inside it, attempting to access the cloud with more unmanaged than managed devices, this principle is modified to say that access to cloud features and data must be consistently verified before being trusted.
Why is SaaS security important?
A startling statistic for every CIO and CISO – estimates of the number of SaaS applications used by an average organization today range between 80 to 140 different applications. In addition to sheer volume, very often these applications, in categories such as ERP, HR, CRM, and R&D, contain an organization’s most confidential data. While the confidentiality, integrity, and availability of SaaS applications is critical to most businesses, this “SaaS sprawl” makes securing SaaS very challenging, especially given today’s shortage of cybersecurity resources. Securing SaaS applications should often be a primary goal of a proactive Enterprise Security Program, and yet we find there continues to be major gaps in understanding of user’s responsibilities and proper attention paid to setting and continuously validating SaaS security configurations.
How do you manage security in the cloud?
In cybersecurity overall, the no-win approach of constantly reacting to threats is no longer practical, especially in these days of scarce security resources. In addition to best practices, cloud security management includes integration, automation, and adaption, focusing efforts and spending on attack surface reduction, or preventing attacks by hardening security controls, and lowering risk, threat volumes, and overall costs. An active protection system, providing granular control, can greatly assist security teams in managing security in the cloud.
Have More Questions?
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.
