Microsoft Sentinel, MDR, and MXDR Services
Unsure if Microsoft Sentinel and SecureSky services are right for your organization? Take The QuizContact UsWhat We Do
Microsoft Sentinel Design, Deployment, Enablement, and Management >
- SIEM feature and functionality comparison and use case analysis
- Architectural and log retention design
- Log volume quantification and Azure consumption cost estimation
- Supported and custom data source connectivity
- Threat intelligence enablement
- Alerting rules, workbooks (visualizations), and query development
- Workflow and orchestration development for both analyst-triggered and automated response
- Proof of Concept design, delivery, and analysis
- SecOps training and integration into your security program
Managed Detection and Response (MDR) and Managed XDR (MXDR) >
- Identification of and support for improvements to reduce threat volumes
- Threat detection and response
- Integration of additional Microsoft security tools into threat analysis
- Scenario-based, free form, and triggered threat hunting
- Configuration and patching tracking
- Ongoing Microsoft Sentinel / Azure cost management
- Additional data source connectivity, security content and automation development
- Microsoft Security (XDR/Defender) management and development
- Microsoft Sentinel management and maintenance
- Continuous SecOps training
What is Microsoft’s Security Information and Event Management (SIEM) Platform?
Microsoft Sentinel is a cloud native SIEM that aggregates data from multiple sources, including users, applications, servers, and devices running on-premises or in any cloud, allowing for the analysis of millions of records, using artificial intelligence to scrutinize threat data. A high number (and growing) of supported data source connectors enable rapid onboarding of many security solutions, as well as provide for open standards such as CEF and Syslog.
Microsoft Sentinel addresses many of the issues that plague traditional SIEMs – eliminating the cost and time associated with deploying hardware or virtual data collection appliances, allowing for speedy connectivity to security logs data sources, and providing quick visibility into risk and security threats across multi-cloud and hybrid environments. Sentinel provides efficient data queries, intelligent security analytics, and an advanced security orchestration automation and response (SOAR) engine.
Microsoft Sentinel provides native bi-directional connectivity to additional Microsoft security hubs such as Microsoft 365 Security Center and Microsoft Defender for Cloud (formerly known as Azure Security Center). Sentinel also connects directly to individual Microsoft products, for example Microsoft Teams, Defender for Cloud Apps (formerly known as Microsoft Cloud App Security, or MCAS), Defender for Identity, and Defender for Endpoint.
Microsoft Sentinel Structure
Microsoft Sentinel is cloud native and built on the Azure infrastructure, allowing for cloud scale and flexible security, while reducing security infrastructure setup and maintenance. Together with Azure Log Analytics, this enables rapid connection to collect data from a wide spectrum of data sources, pre-built functionality, visibility to multi-cloud and hybrid environments, and powerful intelligent security analytics.
Log and Event Source Types: Microsoft Sentinel can ingest security logs and events from Azure and Microsoft 365 tenants, including Microsoft Teams, third-party IaaS (for example, AWS and GCP) and SaaS sources, and on-premise sources. A majority of connections can be made via Microsoft native connections, Microsoft/OEM supported connectors, or using a lightweight agent. Custom data connectors can also be created, using specially developed parsers, Azure Functions or Azure Logic Apps.
Analytics: Security analytics are provided from a combination of Azure services, for example Azure Log Analytics and Machine Learning Service Workspaces.
Visualizations: A multitude of graphical representations of data can efficiently be deployed or developed with Azure Dashboards, Azure (Jupyter) Notebooks, or using Power BI functionality.
SIEM and SOAR: Finally, the Microsoft Sentinel layer provides security aggregation, cross-platform analysis, and SOAR Playbooks, with automation functionality for workflow and orchestration, as well as the capability to apply artificial intelligence models using Azure AI and other available tools.
SecureSky’s Deployment and Enablement Methodology
SecureSky has years of hands-on experience in building, deploying, and managing legacy and cloud native SIEMs, and has implemented Microsoft Sentinel for clients in a wide variety of sectors, and for an extensive range of data sources, architectures, and use cases. With each deployment we evaluate where things went well and where we encountered obstacles and have developed a process that greatly helps to ensure a successful SIEM deployment. The major phases of this approach are below.
1. Scope Discovery and Assessment
In this initial discovery phase, it is important to gather information about the current state of the organization’s threat detection and response capabilities, such as:
- Existing platforms used for managing security incidents
- What system logs and machine data best help identify unusual or suspicious activity
- Associated “normalized” volumes of these logs
- Gaps in current visibility or functionality
- Existing and desired new use cases
- Compliance mandates the company falls under that require log retention for certain periods of time
The next step is to understand the organization’s objectives from a business strategy and IT roadmap perspective, to determine:
- Possible product or service migrations to new security data sources
- Potential regional or business unit expansion that may require log collection segmentation or access controls, to meet confidentiality or data sovereignty requirements
- The company’s DevSecOps model, including current and anticipated staffing levels and training requirements
This last item is especially important, as deploying a new SIEM can have a disruptive impact on the organization’s security operations, if not properly planned. SecureSky’s approach is to provide both formal knowledge transfer and OTJ support at key junctures of the deployment, and if eXtended Detection and Response Services are chosen, throughout the life of the engagement.
Of course, change is the only constant in most entities, so in the next phase, Planning and Design, it is critical architect the implementation with the most flexibility and speed-to-value, to be able to adapt to future unknowns.
In identifying gaps and use cases, especially if the organization is migrating from an existing SIEM, at the end of this phase the success criteria of the deployment should be clearly defined. An additional element for discussion is the organization’s appetite for applying zero trust principles, and the potential for related responses automation versus user impact.
Finally, while the consumption-based pricing model of Microsoft Sentinel is certainly desirable, it can be a challenge to estimate, especially if new data sources are being introduced, or there is a staged approach to the deployment or additional sources from which to collect data. In this phase, SecureSky assists our clients with both education related to the Microsoft Sentinel pricing elements and log retention options, and with log volume and pricing calculators for estimating future costs.
2. Planning and Design
The deployment plan will document the goals, timeline, and approach for implementing the project deliverables. If the implementation is complex or multi-staged, this approach will include the agreed upon design or architecture, and the order of deploying specific data sources, log aggregation regions, or other project variables.
The project plan will also include an agreed upon project management and governance structure, including status meeting or reporting requirements, as well as change management and escalation processes if an obstacle is encountered, or client business needs re-prioritize deployment elements.
3. Data Source Onboarding
The deployment now turns to the initial ingestion of security data into Microsoft Sentinel. SecureSky will provide any needed support to create the cloud native Microsoft Sentinel instance, propagate any collection agents, or create on-premise logging aggregation functionality, such as a System Logging Protocol (Syslog) server.
Next, based on the prioritized order of data sources to be deployed, SecureSky will configure Microsoft native or Microsoft/OEM supported connectors, or develop custom connectivity mechanisms, using specially developed parsers, Azure Functions or Azure Logic Apps.
At the conclusion of any needed troubleshooting or additional configuration, SecureSky will begin a normalization phase for each data source, to initially establish standard volumes throughout a day, week, or month timeframe (and, working with our client, define any additional anticipated changes based on seasonality or other events).
During this time, SecureSky will also begin to deploy the security content associated with the data source, including standard and custom developed dashboards (workbooks), alerting or anomaly detection rules, and queries to be used for threat hunting and investigation, as well as integrate both open source and client acquired or curated threat intelligence data.
4. Analysis and Tuning
- Reduce false positive results
- Improve the threat detection value of the data by adjusting alerting or detection policies
- Modify workbooks or queries to provide better utility
This stage also allows SecureSky to evaluate specifics from the client environment related to the various log types from each data source and begin to apply the cost management parameters established in the earlier phases, to ensure the intended security data is being collected, and non-valuable data is pruned out.
Finally, SecureSky will review threat triggers and volumes, and begin to identify security controls that, if implemented, will reduce threat volumes.
5. Optimization and Automation
The last deployment phase builds on the previous one, by assisting SecureSky clients with the implementation of control improvements or attack surface reduction techniques, to decrease threat volumes.
In this phase, SecureSky will also deploy and test any in-scope (or identified during the deployment) automation opportunities for security workflow or orchestration (SOAR) functionality, a key benefit of Microsoft Sentinel. Of course, automated actions can also be implemented at a later date, once the client has had a chance to further utilize the SIEM.
It is important to note that best practices to maximize SIEM value prescribe that these last two phases be iterative and ongoing throughout the life of the SIEM. If SecureSky is engaged to provide Managed XDR Services, described below, we will continue to tune, adapt content, manage costs, and seek improvements to lower risk and threat volumes. If SecureSky’s involvement does not continue, at the conclusion of this phase, SecureSky will conduct a client workshop, to train stakeholders on the deployment lessons learned and ongoing processes to optimize Microsoft Sentinel.
Contact SecureSky For More Information About Microsoft Sentinel Deployment and Enablement Services
Deployment and management of a SIEM can be complicated and time-consuming for any organization. SecureSky’s experience helps fast track your Microsoft Sentinel deployment, to help you realize true security value quickly and efficiently.
Managed Detection and Response (MDR) and Managed XDR (MXDR) Services
Outsourcing all or part of your Security Operations to a Managed Security Service Provider (MSSP) or Managed Detection and Response (MDR) provider, can be a daunting task these days. With so many vendors, using so many different technologies, and making so many claims, who can you believe?
Helping you detect and respond to security threats is expected. Beyond these “table stakes,” SecureSky’s Managed XDR Services are different.
Our comprehensive approach is designed to help your organization:
- See deeper and wider in your environment for indicators of compromise
- Head off threats by applying protective controls, before they create disruptive business problems
- Actively manage the cost of your SIEM investment
- Train your hard to attract and retain cybersecurity resources
- Have ultimate flexibility, and not be held hostage by a MSSP/MDR vendor’s proprietary SIEM platform
SecureSky’s MDR/MXDR services include coverage of cloud, on-premise and hybrid environments, incorporate our patented Cloud and SaaS Security Posture Management (CSPM/SSPM) platform, prioritize optimizing your defenses over constantly chasing threats, and help you maximize your investment in a SIEM platform.
Expanded Detection and Protection
Legacy Managed Detection and Response (MDR) services typically monitor security devices or services such as firewalls, IPS/IDS, WAF, and DAM technologies, with some providers adding server and workstation endpoint monitoring.
With most organizations operating in a hybrid scenario, and including multiple cloud IaaS and SaaS services, SecureSky MDR/MXDR services go well beyond legacy coverage, providing both cloud threat detection and response and security posture management, for complete risk and threat management. SecureSky’s MDR/MXDR services approach includes:
- Identity and access management (Azure AD) *
- On-Premise (Managed) Detection and Response
- Cloud Detection and Response *
- Endpoint Detection and Response (EDR) *
- Cloud and SaaS Security Posture Management (CSPM/SSPM)
In addition to this expanded detection and protection portfolio, SecureSky’s Proactive Managed Security Services (MDR and MXDR) provides expertise in enabling XDR product suites, optimizing your environment for full protective capabilities.
* While SecureSky supports many cloud and endpoint security data sources, if your organization utilizes the Microsoft security stack, Microsoft Sentinel includes native bi-directional connectivity to additional Microsoft security hubs and direct connection to individual Microsoft security products.
SIEM Plus Cloud and SaaS Security Posture Management (CSPM/SSPM) Technology
SecureSky’s Managed XDR technology stack includes two key components:

Microsoft Sentinel
A next-generation cloud native SIEM, to provide security log collection, advanced analytics for detection of anomalies and indicators of compromise, modern visualization capabilities, and state-of-the-art security orchestration, automation, and response (SOAR) functionality.
SecureSky’s Active Protection Platform
Our industry leading Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) tool, to continuously assess security configurations and detection policies in cloud services, and assist with protective hardening, threat hunting, and investigations.
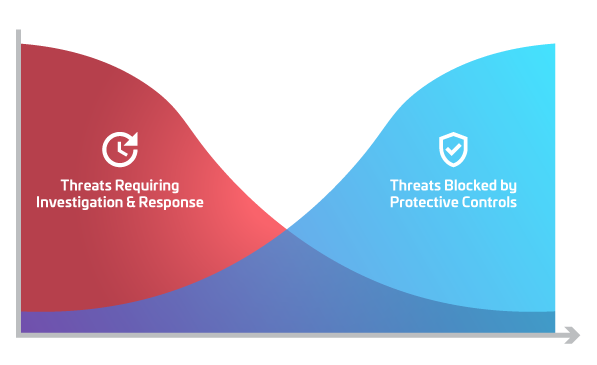
Threat Resolution with Continuous Security Improvement
Using the extensive SecureSky technology stack to provide extended visibility, SecureSky’s Proactive Managed Security Services (MDR and MXDR) provide 24/7 monitoring, triage, escalation, and response for critical and high severity security alerts, as well as expert-level support for our client’s security operations groups.
Unfortunately, constantly reacting to threats is a no-win game. Attack vectors and threat volumes continue to increase, while human cybersecurity resources continue to be in very short supply.
SecureSky’s Proactive Managed Security Services (MDR and MXDR) approach is different, focusing on threat hunting, and detailed review of security alerts, trends, and expected user behaviors to identify and prioritize protective hardening actions to reduce the attack surface and related threat volumes.
Ongoing Cost and Product Optimization
SecureSky’s Proactive Managed Security Services (MDR and MXDR) Services also includes assistance with managing your security investments.
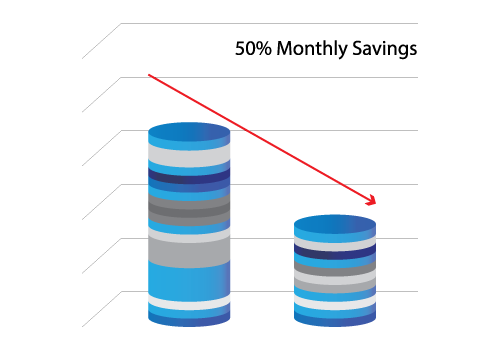
Cost Management
SecureSky’s Proactive Managed Security Services (MDR and MXDR) continuously collects data to monitor log volumes, generated security alerts, and the risk and threat landscape, to balance security value with log ingestion and retention costs. We work closely with our clients to actively manage their SIEM processing and log retention costs.
License Utilization
In today’s rapidly changing and often confusing security technology world, functionality is often available that can offer organizations cost savings by eliminating redundant products, or improved security from integration. SecureSky XDR assists our clients with evaluating and maximizing what they are already paying for, or as they review potential migrations.
Training and Transferability
SecureSky wants to retain our clients by providing value at every opportunity. In addition to the advanced functionality of Microsoft Sentinel, the beauty of developing a separate SIEM technology is, if we do not fulfill our end of the bargain, you can take your SIEM in-house, or to another provider. And we are more than “OK” with that.
Of course, outsourcing and then insourcing elements of your SecOps, doesn’t work if your internal resources are not adequately trained. SecureSky prides itself on training of our clients. Whether formal workshops or OTJ knowledge transfer in development of Microsoft Sentinel, in response to an alert, or in remediation of a security control or policy, SecureSky will prepare and support your staff.
Frequently Asked Questions
What is the difference between Microsoft Sentinel and Azure Sentinel?
They are the same. Originally named Azure Sentinel, in late 2021 Microsoft renamed several Azure-based security products with the Microsoft brand, indicating their ongoing investment in these tools to manage the security posture of, and take signals from, a wide variety of non-Azure workloads.
Why should I use the Microsoft SIEM/SOAR platform?
Microsoft Sentinel is a powerful cloud native SIEM and SOAR platform, which can analyze security data across an entire organization and intelligence signals from across the globe. Offering integrated security orchestration, automation, and response (SOAR) functionality, Microsoft Sentinel helps to protect against today’s often complex attack vectors.
What is the difference between Azure Security Center and Microsoft (Azure) Sentinel?
Azure Security Center is a security management system, assessing the security status of IaaS environments, providing configuration recommendations to prevent threats, and raising native security alerts. Microsoft (Azure) Sentinel is a highly scalable security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution that analyzes a broader range of security and threat intelligence data sources, incorporates intelligent security analytics, and provides a unified solution for alert detection, threat visibility, proactive hunting, and threat response.
What is a Microsoft Sentinel workbook?
An interactive dashboard from one or multiple data sources, designed to provide security practitioners visual reporting and analysis to make timely and insightful security decisions.
What does the Microsoft platform monitor?
Security logs and events from a multitude of data sources, including Azure and Microsoft 365 tenants, including Microsoft Teams, third-party IaaS (for example, AWS and GCP) and SaaS services, and on-premise devices.
How does Microsoft Sentinel collect data?
A majority of data connections are made via Microsoft native or Microsoft/OEM supported connectors, or using a lightweight agent. Custom data connectors can also be created, using specially developed parsers, Azure Functions or Azure Logic Apps.
Is the Microsoft technology a SIEM or a SOAR?
Both. Microsoft (Azure) Sentinel is a highly scalable security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Utilizing artificial intelligence, Microsoft Sentinel analyzes a broad range of security and threat intelligence data sources, incorporates advanced security analytics, and provides a unified solution for alert detection, threat visibility, proactive hunting, and threat response.
Is Microsoft Sentinel a SOC?
Microsoft Sentinel is an advanced SIEM (security information and event management) and SOAR (security orchestration, automation, and response) product, which can be used as the primary technology platform for a SOC (Security Operations Center). SecureSky uses Microsoft Sentinel as one solution supporting their Managed XDR Services.
Is the Microsoft SIEM/SOAR technology required to run the Microsoft Defender product line?
No, however dependent on the size of your organization and the amount of Microsoft Defender products deployed, using Microsoft Sentinel to collect data from the Microsoft Defender series can greatly help to aggregate and analyze large quantities of data.
In 2020 Microsoft began renaming several of its cybersecurity offerings using the Microsoft Defender brand. Microsoft Defender now serves as Microsoft’s umbrella “XDR” brand, used to describe their products that detect and respond to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms.
While the Microsoft Defender series is an extremely valuable toolkit, it can be complicated to understand and configure. There are many current and developing products in the Microsoft Defender suite, divided primarily into protecting Microsoft 365 users and IaaS/workload clients (to make matters even more confusing, this latter family of products was named Azure Defender for a period, until Microsoft switched their brand identity to Microsoft Defender to denote some products provide coverage beyond Azure).
For assistance in interpreting the Microsoft Defender product and licensing puzzle, properly configuring Microsoft Defender products, and integrating the data into Microsoft Sentinel, please contact SecureSky.
Have More Questions?
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.
