Cloud Security Assessment
Contact UsWhat We Do
- Provide cloud security assessments across a wide range of leading SaaS and IaaS platforms, identifying cloud security vulnerabilities before security breaches occur
- Assess protective controls and detection policies, incorporating industry standards, leading security benchmarks, and compliance mandates, as well as SecureSky best practices proprietary checks
- Include compensating controls to provide a comprehensive picture of cloud security risks and recommended security solutions
- Provide actionable recommendations to strengthen the environment and improve data protection
- Assist with remediation design, deployment, and testing


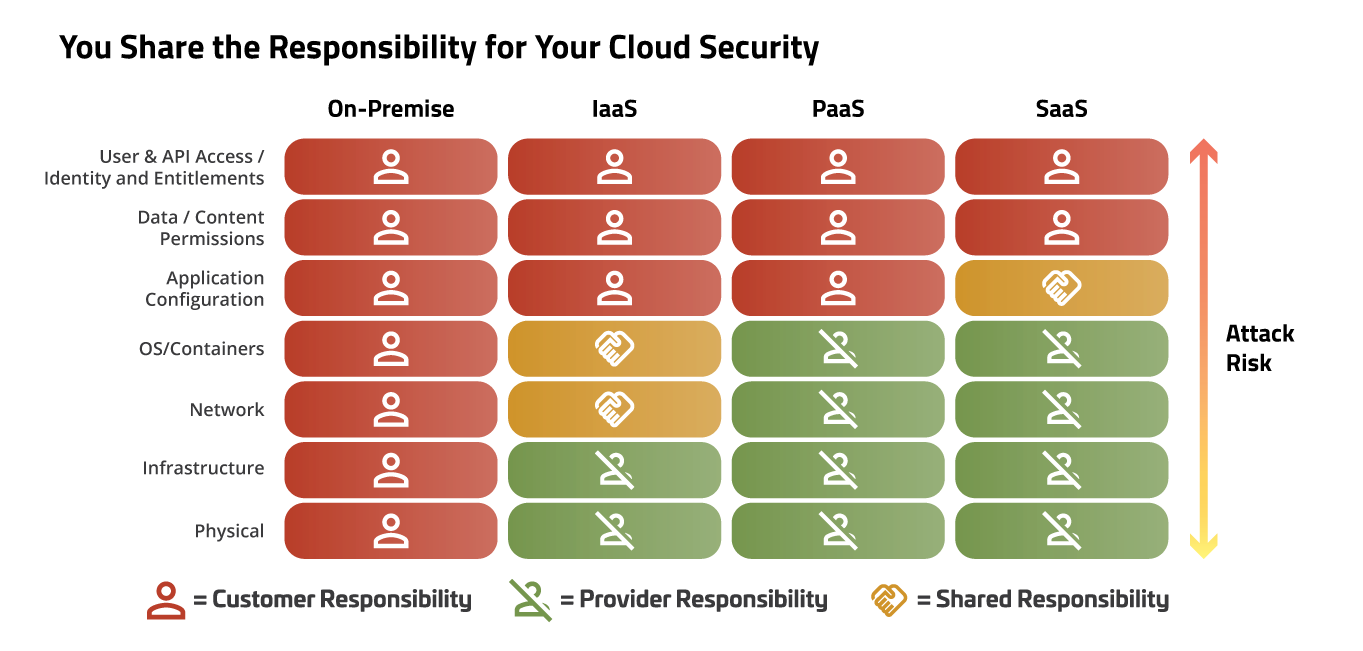
Configuration of many elements of cloud resources is the responsibility of the buyer, and misconfiguration of these resources is a leading cause of vulnerabilities which can lead to compromise, including exposure of sensitive data. Cloud security assessments define the critical security controls and detection policies needed to deter attacks, identify gaps in your current state, and provide prioritized corrective measures to properly secure the cloud environment. SecureSky’s security experts provide cloud security assessments to establish a security baseline, and ongoing solutions to make sure that position does not inadvertently or maliciously deviate from its hardened state.
A considerable challenge in providing cloud security assessments is determining the basis for security hardening recommendations. As vendors rapidly modify their security, identity, and regulatory compliance functionality, defining the desired state of multiple applications and platforms requires constant attention. SecureSky, works closely with the Center for Internet Security (CIS), a recognized authority on creating and documenting recommended security configurations and best practices. SecureSky are co-editors and contributors to several CIS Foundations Benchmarks, and bases the findings of our cloud security assessments on these proven best practices and compliance standards. Security assessment recommendations are prioritized by:
- Security and compliance risk
- Compensating controls or technologies
- License levels
- User impact
- Deployment level of effort
Upon completion of a cloud security assessment, SecureSky offers remediation support and ongoing technology and services based on these same best practices, to guard against configuration drift, identify new capabilities from cloud platform providers, and help our clients maintain and continuously improve their hardened environments.

Identify Gaps in SaaS and IaaS Protective Security Controls
The rapid adoption of cloud services, greatly accelerated by the recent pandemic, has created substantial risk management concerns for many organizations. In addition to inadequate protections from risk, SecureSky finds a majority of entities do not have appropriate monitoring in place to detect and respond to threats arising in or from cloud services.
Cloud providers do not, or cannot, take full responsibility for many security controls or threat detection policies in client environments. Each has some form of “shared responsibility model” as illustrated above, indicating user responsibility for data integrity and confidentiality, endpoint security and account, access and identity management. Gartner has been widely quoted as saying 99% of cloud security failures will be the customer’s fault, mainly in the form of the misconfiguration of cloud resources.
Cloud providers want users to easily purchase and adopt their product. That’s the business they are in. Their flexible and rapid deployment models, intended to be “frictionless,” often come with inadequate default configurations for security, privacy, compliance, and threat detection.
Many cloud providers use a distribution model of selling licenses via channels, who have the same sales motivation. Managed Service Providers (MSPs) and Cloud Service Providers (CSPs) can also create a false sense of security with buyers by indicating they are performing security functions, when in reality they are providing limited configuration without a thorough understanding of the buyer’s risk or current attack vectors.
No matter how many third-party providers are involved, ultimately the security of cloud services, as well as the ability to detect and respond to threats, falls on the buyer.
SecureSky’s cloud security assessment evaluates configurations and detection policies in cloud application, platform, and infrastructure services, aligning our cloud security assessments closely with your company’s use cases, risk profile, and objectives.
SecureSky’s security experts assess current configurations and settings and detection capabilities, comparing these findings against industry-leading security benchmarks, best practices, and compliance standards, many of which have been developed in whole or in part by the experts at SecureSky.
Finally, a cloud security assessment of an individual cloud infrastructure or SaaS platform in a vacuum can provide erroneous results. Many organizations have third-party intrusion controls, identity management, data exfiltration protections, or monitoring solutions in place outside of a specific cloud platform. These functions must be accounted for to properly assess cloud security risks, as well as to not create an inaccurate audit trail. SecureSky’s cloud security assessments take into account such compensating controls to provide a true report of risk items and recommended remediations.
In addition to considerations for previously implemented technologies, we also work closely with our clients to coordinate our analysis with the company’s policies, risk profile, and budget to create a realistic action plan to address risk.
Remediation Recommendations
SecureSky’s prevailing philosophy is to assist our clients in creating protections, to reduce the need to constantly react to threats. This approach is especially needed given today’s scarcity and cost of cybersecurity resources.
SecureSky’s cloud security assessments provide detailed recommendations for improving our clients’ protective controls and detection capabilities, clearly articulating the reasoning and compliance reference behind each recommendation, the priority of each recommendation, the estimated level of effort for each security enhancement, and the potential impact of the change on the organization’s users.
Our team of experienced consultants will thoroughly present and discuss our findings with all client stakeholders, to ensure a complete understanding of the finding, and recommended remediation actions. SecureSky can also assist SecOps groups with executive communications to create awareness and support throughout the organization.
Remediation and Security Initiative Support
A SecureSky cloud security assessment goes well beyond making remediation recommendations, providing expert resources to assist our clients with architecting, deploying, enabling, and testing security controls and detection policies within SaaS and cloud infrastructure (IaaS) platforms. Upon completion of remediation actions to address security misconfigurations, we also provide re-testing, to validate that work performed resulted in the intended outcome of an improved security posture.
Inside and outside of specific platforms, often a cloud security assessment also uncovers capabilities that are licensed and underutilized, presenting either improved functionality, better integration, or cost savings. SecureSky experts can also assist you with the design, deployment, testing and enablement of security technology, with a specialization in the Microsoft 365 security suite.
Contact SecureSky for a Free Cloud Security Consultation
Going Beyond Point-In-Time Assessments
Continuous Cloud and SaaS Security Posture Management (CSPM/SSPM) and Managed eXtended Detection and Response (MDR/XDR)
SecureSky’s Active Protection Platform
SecureSky’s patented Cloud and SaaS Security Posture Management system, the Active Protection Platform, provides ongoing continuous cloud security assessment, with functionality providing:
- Multi-cloud monitoring, visualization, and risk prioritization of SaaS and IaaS environments
- Continuous cloud security and compliance configuration and detection policy assessment and validation, based on industry-leading benchmarks such as Center for Internet Security (CIS) Foundations Benchmarks
- Available enforcement of hardened security configurations
- Collection of security threat data
- Streamlined and automated threat response actions
- Functionality to generate reports for auditing, forensics, and operational requirements
Managed eXtended Detection and Response (MDR/XDR) Services
In addition to advanced SIEM and SOAR technologies, SecureSky’s managed detection and response services (MDR/XDR) also utilize our Active Protection Platform, with ongoing continuous cloud security assessment, to develop, deploy, validate, and enforce cloud security configurations/protective controls and detection policies, to reduce risk profiles and thus threats requiring investigation.
Client-Dedicated Analysts
- Threat analysts, forensic investigators, and engineers with deep security, Cloud and SaaS Security Posture Management, Microsoft Sentinel, and incident response experience
Microsoft Sentinel Management
- Proactive threat hunting, driven by timely threat intelligence indicators
- Continuing custom development of data connectors and Microsoft Sentinel workbooks, queries, enhanced parsing, tuning and automation, workflow, and orchestration opportunities
Security Optimization
- Advanced Microsoft security suite enablement
- Attack surface reduction
- Security control validation
Security Technical Sessions and Business Review
- Training and knowledge transfer, to ensure client team awareness and updates
- Ongoing cost analysis, technical, and business reviews
Frequently Asked Questions
What is included in a cloud security assessment?
A cloud security assessment analyzes an organization’s cloud-based infrastructure and application environments to assure that the organization is protected from a wide variety of security risks and threats.
SecureSky’s cloud security assessment evaluates IaaS, PaaS and SaaS security and detection policy parameters, comparing the current state of the cloud environment to best security practices, as defined by Center for Internet Security (CIS) benchmarks, and other cloud security standards.
At the conclusion of a cloud security assessment, a report is provided describing the environment’s configurations which are compliant with best security practices, and those which are not. For areas where gaps from best practices are identified, SecureSky prioritizes recommended remediation based on compensating controls, license levels (availability of certain product functionality), deployment efforts required, and potential impact to users. Recommendations are presented and discussed with our clients and following the cloud security assessment we remain available for additional consultation and re-testing.
Who is the intended audience for a security assessment report?
There are multiple audiences for a cloud security assessment report, including:
- IT or SecOps teams with limited cloud experience or expertise, desiring to use findings both as a basis to harden their environment and as a training tool.
More mature IT or SecOps teams wanting an independent, third-party check of their configuration design and any drift from that design. - Compliance personnel wishing to self-assess or prepare for regulatory audits.
- Compliance, legal, or customer service teams with contractual requirements requiring a security assessment and related client reporting.
- Compliance, legal, sales, or marketing groups wanting to substantiate marketing claims.
- IT or SecOps executives, other business leaders, or Board members wanting to measure security accomplishments or receive an independent, third-party evaluation of their environment.
What is cloud security?
Cloud security is inclusion of cloud environments (IaaS, PaaS, and SaaS) into an organization’s Enterprise Security Program, including continuous risk management, the application and adaption of protective controls to ensure confidentiality, integrity and availability of resources, and threat detection and response performed in a resilient manner, to rapidly withstand and recover from malicious attacks. Dependent on the organization’s usage of cloud resources, the responsibility for risk management, protective controls, and threat response is shared between the cloud provider and customer.
Who needs cloud security?
As published by every major cloud provider, the “shared responsibility” model communicates to all customers of cloud services their accountability for multiple elements of cloud security. Based on their usage of cloud infrastructure, platform, or software services, customers are liable for appropriately configuring security controls and threat detection policies for their applications, data, and user identities and access.
What is the difference between CSPM and SSPM?
CSPM is an acronym for Cloud Security Posture Management, a technology to identify weaknesses such as misconfiguration issues, compliance risks, and detection policy shortcomings in cloud infrastructure (IaaS) services, such as Microsoft Azure, AWS, or GCP, and often to provide additional functionality such as enforcing related hardened security policies. SSPM is an acronym for SaaS Security Posture Management. As the name communicates, this technology provides similar functionality for SaaS, or cloud-based applications, such as Microsoft 365, Google Workspace, Okta, or Salesforce.
What are the benefits of cloud security?
As with all cybersecurity measures, whether to protect cloud or on-premises environments, the benefits of cloud security are maintaining the confidentiality and integrity of input and derived sensitive information, the efficacy of processes, and the availability of resources. Properly securing a company’s digital assets provides efficiency (with related cost savings) for an organization’s internal users, and, if applicable, reliability (with related competitive advantages) for external users.
What are the challenges in cloud security?
There are numerous security challenges in the cloud, beginning with awareness of an organization’s presence in the cloud. Often coined “shadow IT”, it is very simple for users to spin up cloud or SaaS instances in a matter of minutes, without a thorough understanding of security protocols. The nature of cloud computing also dissolves traditional network boundaries, leading to user identification, access and entitlement management becoming the focal point of controls, as well as user behaviors often being a primary indicator of risk. Another challenge is the sheer volume of cloud usage. The recent COVID-19 pandemic accelerated the already rapidly growing adoption of cloud computing. Only counting SaaS applications, estimates range from an average company using between 80 to 140 different applications. This “SaaS sprawl” and related explosion of all cloud services makes multi-cloud monitoring and management almost impossible. Finally, as in all cybersecurity fields, the shortage of human resources with cloud security expertise, especially as attack volumes grow daily, is a major concern.
What are the types of cloud security?
There are many categories of products and services that can be used to secure cloud assets, many of which are cloud-based services themselves. These cloud security tools provide functionality for user identification, multi-factor authentication, controlling access, entitlement management, email phishing or malware deterrence, data protection and data loss prevention, limiting access to risky applications, and IaaS and SaaS secure configuration management (cloud security posture management).
What is a cloud security model?
An effective cloud security model incorporates several integrated technologies and intelligence sources, with automation and adaptive response capabilities. At the core of this model is the “Zero Trust” principle. Traditional network based Zero Trust says that users, systems or services operating inside the network must be identified and authenticated with each system or service they are attempting to access. In today’s cloud computing world, where there are more users, systems or services outside an enterprise than inside it, attempting to access the cloud with more unmanaged than managed devices, this principle is modified to say that access to cloud features and data must be consistently verified before being trusted.
Why is SaaS security important?
A startling statistic for every CIO and CISO – estimates of the number of SaaS applications used by an average organization today range between 80 to 140 different applications. In addition to sheer volume, very often these applications, in categories such as ERP, HR, CRM, and R&D, contain an organization’s most confidential data. While the confidentiality, integrity, and availability of SaaS applications is critical to most businesses, this “SaaS sprawl” makes securing cloud applications and preventing unwarranted access to data very challenging, especially given today’s shortage of cybersecurity resources. Securing SaaS applications should often be a primary goal of a proactive Enterprise Security Program, and yet we find there continues to be major gaps in understanding of user’s responsibilities and proper attention paid to setting and continuously validating SaaS security configurations.
How do you manage security in the cloud?
In cybersecurity overall, the no-win approach of constantly reacting to threats is no longer practical, especially in these days of scarce security resources. In addition to best practices, cloud security management includes integration, automation, and adaption, focusing efforts and spending on attack surface reduction, or preventing attacks by hardening security controls, lowering risk, threat volumes, and overall costs.
What are the top Microsoft 365 security challenges?
Microsoft 365 is one of the most highly utilized SaaS products in the world. In addition to an email service, the productivity and collaboration suite includes cloud file storage (SharePoint) and an A/V interactive tool (Teams). Microsoft 365 also includes Azure Active Directory (AD), an identity and access services used by many companies. This combination of components makes Microsoft 365 a highly lucrative target for attackers.
Because Microsoft 365 offers such broad functionality, as well as is typically deployed as an enterprise-wide application, some of the primary security risks of Microsoft 365 are sensitive data leakage and credential theft, which often leads to business email compromise (BEC) and account takeover (ATO).
The good news is Microsoft 365 can be secured to address such risks, as well as be used as a tool to provide protection against broader security threats arising from cloud computing, including identity and access management, and storing sensitive data. such as personally identifiable information, in the cloud.
Is securing Microsoft 365 difficult?
Properly configuring security controls and detection policies in Microsoft 365 involves navigating multiple portals, mastering differences between sometimes confusing and rapidly changing licensing options, and understanding dependencies and compensating controls between other Microsoft and third-party technologies. Those wanting to manage Microsoft 365 and Azure AD using PowerShell or APIs experience even greater complexity.
Properly securing Microsoft 365 requires a knowledge of its configuration parameters, a hardening basis (such as the Center for Internet Security Foundations Benchmark), the ability to navigate to the appropriate locations to set the proper configurations, and finally, a tool to validate on an ongoing basis that your secure settings have not been modified and enforce them if they inadvertently or maliciously tampered with.
SecureSky’s Security Configuration Assessment for Microsoft 365 and Active Protection Platform provides all of this functionality, enabling our clients to quickly assess their Microsoft 365 tenants, adjust configurations based on best practices, and continuously monitor and manage hardened environments.
Have More Questions?
Security Posture Management (CSPM/SSPM)
Active Protection Platform Overview
Active Protection Platform Technology
MDR, Managed XDR (MXDR), and Managed Sentinel
Contact Us
©2022 SecureSky, Inc. All rights reserved. SafetyNET, SecureSky, AdaptiveDefender and the SecureSky logo are marks of SecureSky, Inc. SecureSky U.S. Patent Nos. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239. Additional patents pending. Azure and Office 365 are registered trademarks of Microsoft.